Microsoft Copilot for Security, valuable part of your security team!
Microsoft Copilot is a security solution that uses artificial intelligence and machine learning to protect data and applications in the cloud. It is part of Microsoft 365 and helps developers write higher quality and more secure code. This solution is designed to help organizations protect their critical information while leveraging the benefits of cloud technologies. Copilot is capable of detecting and blocking threats in real-time, enhancing the security of your data and applications. With AI and machine learning, Copilot continuously learns and improves its threat detection capabilities.
Copilot for Security: Protection at the Speed and Scale of AI
Detect Everything You Miss: Copilot for Security provides a clear and understandable overview of your security status from the vast amount of data signals it collects from your cloud services and applications. This allows you to efficiently filter out unnecessary or irrelevant information and focus on key data crucial for protecting your systems and data. Copilot for Security uses advanced AI and machine learning algorithms to analyze and classify data signals based on risk, severity, and priority. This enables it to identify and alert you to suspicious or harmful activities such as intrusion attempts, malware, ransomware, phishing, or DDoS attacks. This way, Copilot for Security helps you detect cyber threats before they cause serious damage, allowing you to respond quickly and effectively and minimize incident impact. Additionally, Copilot for Security provides tools and recommendations to improve your security posture and prevent future attacks, thereby strengthening your defense and resilience against cyber threats.
Stay One Step Ahead of Danger: Ensure your security team has critical instructions and context at their fingertips to respond to incidents within minutes instead of hours or days. Copilot for Security provides essential information such as threat origin, attack method, impact, and vulnerabilities, enabling rapid decision-making and action. Copilot for Security also assists in incident prevention and remediation by recommending best practices and solutions for each situation. It is your reliable partner in cybersecurity, guiding you through the entire incident management process to ensure optimal security for your data and applications.
Enhance Team Expertise: Support and improve the work of junior employees with detailed instructions while reducing monotonous tasks for senior staff, allowing them to focus on strategically important tasks. Copilot for Security enables you to train and develop your security specialists with interactive templates, scenarios, and simulations that provide practical experience and feedback. This maintains a high level of qualification and motivation in your team, ensuring they are prepared for any threat. You can also use Copilot’s automated functions to delegate and resolve routine tasks such as traffic monitoring, anomaly detection, or patch management. This frees up time and resources for senior staff to plan and execute strategic security initiatives.
Integration of Copilot for Security in Practice
- Foundation for Scalability and Security:
Azure Landing Zone sets the stage for scalable and secure cloud operations. It ensures that your cloud environment is not just ready for today’s needs but is also prepped for future growth. - Governance and Compliance:
In a world where data security and compliance are paramount, Azure Landing Zone provides the framework to ensure that your cloud deployments align with governance best practices and regulatory requirements. - Operational Consistency:
By standardizing your cloud setup, Azure Landing Zone enables consistency across your deployments, making managing and maintaining your cloud environment easier.
Why Do CIOs Need Azure Landing Zone?
In this section, we will demonstrate how Copilot for Security can facilitate and streamline the work of security and IT teams using the Microsoft Defender XDR platform to protect their devices, data, and identities. Microsoft Defender XDR is a comprehensive solution integrating several modules like Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Defender for Office 365, and more, providing a unified view of cyber threats and their impact on your organization. Copilot for Security works with these modules, leveraging their rich data sources and analytical capabilities to provide comprehensive information, recommendations, and actions for your security and IT teams.
For example, if Copilot for Security detects suspicious activity on one of your devices, it provides a detailed incident description, including severity, attack source and target, triggered processes, transferred files, and other relevant data. These insights come from Microsoft Defender for Endpoint, which collects and analyzes data on device and application behavior. Copilot for Security helps determine if it’s a false alarm or a real threat and suggests the optimal response, such as device isolation, process termination, file removal, or user contact. You can perform these actions directly from Copilot for Security or from Microsoft Defender for Endpoint.
Additionally, Copilot for Security can check if the affected device is properly configured, updated, and secured, comparing its status with other devices in your network. If it finds any deficiencies or vulnerabilities, it will alert you and suggest measures for their removal or mitigation, such as patch installations, setting changes, or applying security policies. These functions use data and tools from Microsoft Defender for Endpoint and Microsoft Intune, enabling remote device management and security.
Another example is when Copilot for Security detects a suspicious email sent or received by one of your users. Copilot for Security uses information from Microsoft Defender for Office 365, which monitors and protects your email communication from spam, phishing, malware, and other threats. It provides email details such as content, attachments, sender, recipient, and other metadata, determining if it is a legitimate message or an attack. If it’s an attack, Copilot for Security helps identify its target, impact, and consequences. For example, it can tell if the email contained malware executed on the user’s device, if the user clicked a phishing link redirecting them to a malicious website, or if sensitive information was entered into a fake form. Copilot for Security suggests the best response, such as email deletion, attachment quarantine, user warning, password change, or incident reporting. These actions can be performed directly from Copilot for Security or from Microsoft Defender for Office 365.
Copilot for Security also verifies if the affected user is properly authenticated and authorized to access the data and services they use, ensuring their identity is protected from misuse. This information is gathered from Microsoft Defender for Identity, which monitors and protects your identities and their relationships to network resources. Copilot for Security helps identify and prevent identity attacks, such as brute force, session hijacking, or man-in-the-middle attacks. If such an attack occurs, it helps determine the source, target, and impact, suggesting appropriate measures like blocking unauthorized access, terminating suspicious sessions, resetting passwords, or applying multi-factor authentication. These actions can be taken directly from Copilot for Security or from Microsoft Defender for Identity.
These examples show how Copilot for Security effectively collaborates with the Microsoft Defender XDR platform, providing a comprehensive and integrated view of your security environment. This integration helps you better understand the risks you face and take swift, informed actions to protect your organization. Copilot for Security is designed to ease your workload, increase productivity, and improve results. With Copilot for Security, you have an intelligent and reliable assistant guiding you through the entire incident management process, helping you achieve optimal data and application security.
How does Copilot for Security Work
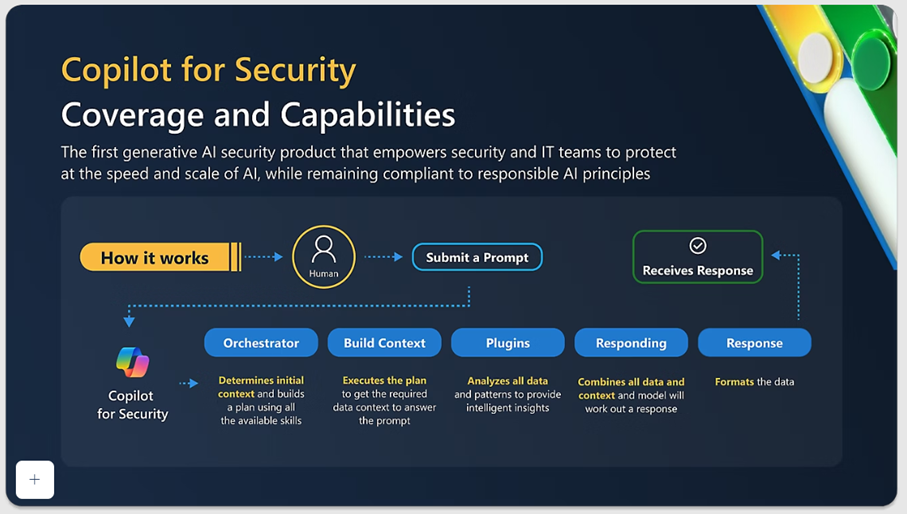
A diagram provides a simplified view of what happens behind the scenes in Copilot for Security when you send a prompt. First, the Copilot orchestrator determines the context and creates a plan using the available skills within Copilot. It then executes the plan, gathering all necessary content and data. Next, it combines and formats the data and context, constructs the response, and implements it. This process can occur within seconds.
Copilot for Security is equipped with a set of skills enabling it to perform various cybersecurity tasks, such as threat analysis, incident reporting, impact prediction, recommending measures, automating tasks, or interacting with users. These skills are based on state-of-the-art machine learning, knowledge graphs, algorithmic logic, and other methods.
Copilot for Security also learns from every query and feedback it receives. This means that the more you use it, the better it understands your needs and adapts to them. Copilot continually expands its knowledge and skills to remain up-to-date and reliable.
Products Integrated with Copilot for Security
- Unified Security Operations Platform
- Microsoft Sentinel
- Microsoft Defender XDR
- Microsoft Intune
- Threat Analysis in Microsoft Defender
- Microsoft Entra
- Microsoft Purview
- Microsoft Defender External Attack Surface Management